Network infrastructures growth in scale and complexity pose the need for modern enterprise automation solutions such as Red Hat Ansible Automation Platform, to cover multi-domain and multi-vendor architectures including standalone and SDN (Software Defined Network) solutions.
Automation is driving network engineer skills transformation and is fundamental for modern network management and operations. Ansible is the de-facto enterprise network automation language and has been pervasive in different network domains, and it is considered one of the network engineer’s skills of the future by Cisco Systems. A quick search in Google will lead more than 5.3 million results, and with such an enormous amount of information it is critical that you can trust that the reference you are using is reliable:
However, there are some considerations to have a successful network automation journey and we are going to address those as part of this blog.
What do you need to automate now and in the future?
Your network will have different protocols and vendors that you should be able to integrate with different platforms to solve multiple use cases, including WAN, LAN, Wireless, Datacenter, Firewalls, IPAM and ITSM. This means you should be able to rely on a rich and trusted ecosystem of integrations to extend your automation capabilities. How can Red Hat help? We have developed and support more than 139 Ansible Certified Content Collections with our partners, including 53 collections that cover network automation devices and platforms.
How are you going to automate your networking use cases in a reliable, repeatable and reusable way?
Know-how should be collective and reusable across teams, and your automation platform should simplify the process of consolidating and sharing proven knowledge. This is important because the tasks and processes you automate will become your building blocks. Think about pre-checks, post-checks, backups and common configurations including routing protocols such as OSPF and BGP, and the interfaces’ management.
To address this knowledge-gap, Red Hat announced Ansible validated content at AnsibleFest 2022. Validated content is designed for you to incorporate over time to perform operational tasks across infrastructure, networking, cloud, security and edge use cases.
As every network is configured differently, Ansible validated content covers a variety of needs, with content available for you to adapt and reuse as a reference in the future.
Now let’s take a look at the validated content that is currently under development, and the collections that have already been released.
What’s available now?
In the last six months, several collections have been released and more are under development. The initial collections available are the following:
network.base collection
This collection acts as the core for other validated content, as it provides the platform-agnostic role called Resource Manager. This validated content collection provides predefined roles and is designed to act as a single entry point to manage all the resources supported for a given network OS.
Some of the capabilities supported are:
- Build Brownfield Inventory: Enabling the capability to get facts for all the hosts within the inventory and store facts in a structured format which acts as the Source of Truth (SOT).
- Supported Resource Query: To get the list of resource modules supported for a given network OS.
- Gather: To gather the facts for specified network resources.
- Persist: To gather the facts for specified network resources and persist those facts into inventory files as host vars, for future reusability.
- Deploy: To deploy the configuration persisted in terms of host vars onto the network devices.
- Configure: To apply configuration in a normalized manner.
You can find additional information on how to use this validated content in this article: Fundamentals of Network Automation with Ansible Validated Content using the network.base collection.
network.interfaces collection
This platform-agnostic Ansible collection helps configure network interfaces as automation resources and provide capabilities to do operational state/health checks. The OS versions supported are: Arista EOS, Cisco IOS-XR, Cisco IOS and IOS-XE, Juniper JunOS and Cisco NX-OS.
Some of the capabilities supported include:
- Build Brownfield Inventory: Users will be able to get the facts for interfaces resources and store the output as host_vars, thus enabling the capability to get facts for all the hosts within the inventory and store facts in a structured format which acts as SOT.
- Interfaces Resource Management: Users want to be able to manage the interface’s general configuration including MTU settings and state, and manage specific Layer 2 and Layer 3 configuration including switchport settings and IP addresses configuration depending on the interface type. This also includes the enablement of gathering facts, updating interface resource host-vars and deploying config onto the selected network devices.
- Interfaces Health Checks: Users want to be able to perform health checks for the network interfaces. These health checks should be able to provide the interfaces admin state and operational state with necessary details.
network.bgp collection
This collection is platform-agnostic by design and allows you to automate multivendor network devices, supporting the following routers and switches OS types: Arista EOS, Cisco IOS-XR, Cisco IOS and IOS-XE, Juniper JunOS and Cisco NX-OS. It also enables teams to configure, and check the status of your BGP (Border Gateway Protocol) configuration as an automation resource.
Some of its capabilities include:
- Build Brownfield Inventory: Users will be able to get the facts for BGP resources and store that information as host_vars, thus enabling the capability to get facts for all the hosts within the inventory and store facts in a structured format which acts as your SOT.
- BGP Resource Management: Users will be able to automate the BGP global and BGP address family configurations. This also includes the enablement of gathering facts, updating BGP resource host-vars and deploying config onto the network devices.
- BGP Health Checks: Users will be able to perform health checks for BGP applications and verify the BGP neighborship status with necessary details.
You can find more details about how to use this collection here.
network.ospf collection
This validated content allows you to configure and check Open Shortest Path First (OSPF) configuration and state, in the same way as the network.bgp collection. It is platform-agnostic and supports the following OS types: Arista EOS, Cisco IOS-XR, Cisco IOS and IOS-XE, Juniper JunOS, and Cisco NX-OS.
This collection includes the following capabilities:
- Build Brownfield Inventory: You can get the facts for OSPF resources and store the results as host_vars in a structured format which can later be your SOT.
- OSPF Resource Management: You will be able to manage the OSPFv2, OSPFv3 and OSPF interfaces configurations. This also includes the enablement of gathering facts, updating OSPF resource host-vars and deploying config onto the network routers.
- OSPF Health Checks: You will be able to automate health checks for OSPF neighbors, and verify the OSPF neighborship status with necessary details.
security.firewall_mgmt collection
This collection helps you build, maintain and validate firewall management and policies across security providers’ firewall appliances. Right now this collection allows us to gather facts and configure Cisco ASA (Adaptive Security Appliance) policies.
network.vpn collection (Beta)
You can use this validated content to build, maintain and validate virtual private network (VPN) tunnels across cloud providers and network appliances.
Using this automation content you can more easily:
- Deploy and validate Amazon Web Services (AWS) and Microsoft Azure tunnels
- Deploy and validate GRE tunnels for your Cisco IOS and IOS XE routers
Where can I find Ansible validated content?
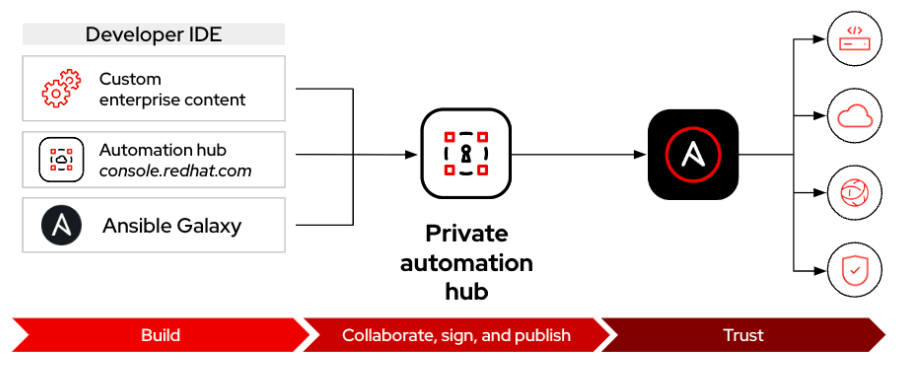
With the release of Red Hat Ansible Automation Platform 2.4, this Ansible validated content, including network-specific collections, will be available in console.redhat.com as well as preloaded in the private automation hub during the installation.
As I have one private automation hub instance up and running, I quickly checked in the Collections > Collections > Validated path and found a myriad of Collections available to use:
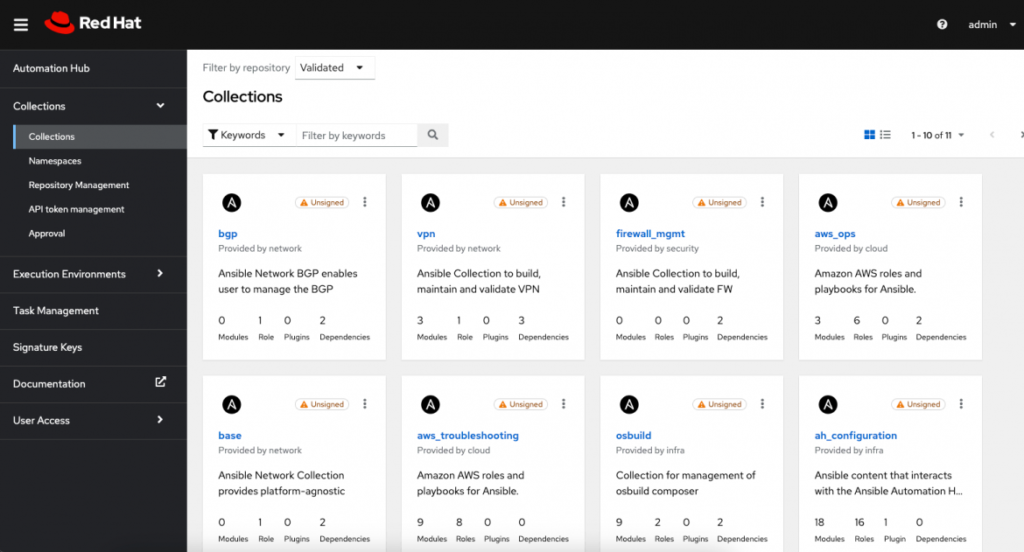
To check further, I opened the BGP collection and I can see the documentation and repo, and even download the tarball file directly.
You can use the Ansible validated content just like you would use any other Ansible Content Collection from private automation hub:
- Use
ansible-builderwith anansible.cfgpointing to your private automation hub and add the collections needed in arequirements.ymlto build an execution environment. - Add a
requirements.ymlfile in your automation controller project and it will pull the Collections from your private automation hub. Note you should have previously configured the private automation hub in youransible.cfg